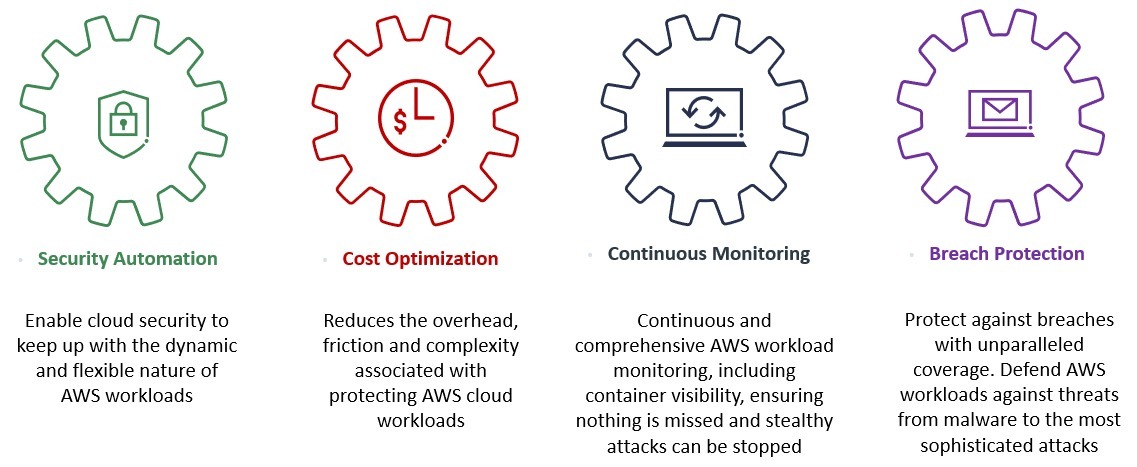
Our all-encompassing defense strategy serves as an unyielding barrier, shielding your priceless data from all possible threats. Our commitment lies in securing your cloud infrastructure while ensuring absolute adherence to vital regulations.
To strengthen security and ensure compliance, we employ sophisticated encryption techniques, multi-factor authentication protocols, and ongoing monitoring procedures, resulting in full protection of your cloud applications.
Our Security and Risk Assessment begins with a Well-Architected Framework Review (WAFR). During this process, we conduct a thorough analysis of the six pillars outlined below.
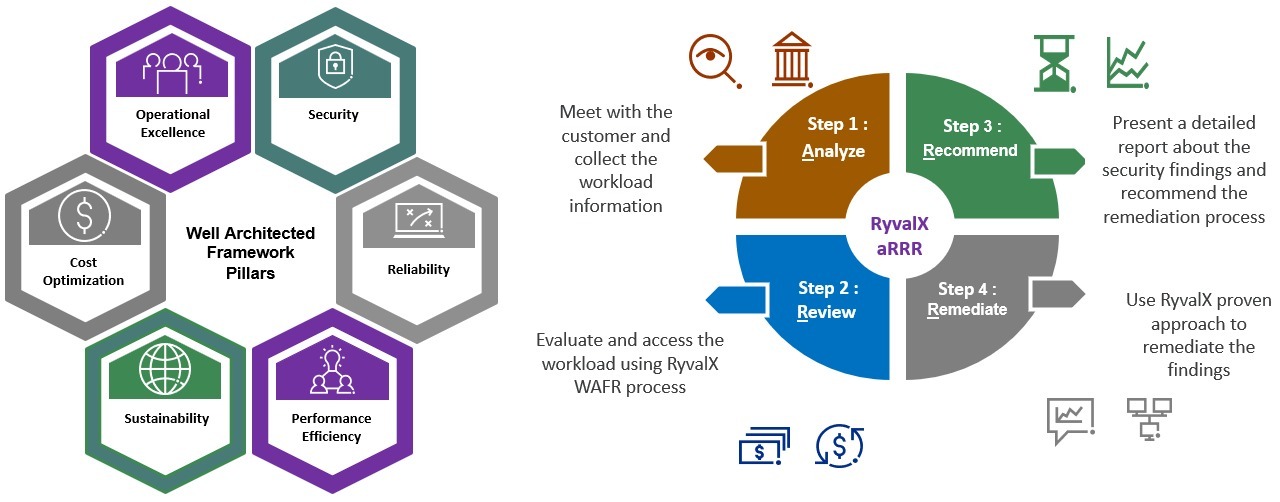
We form a comprehensive framework for a successful cloud migration and deployment journey, ensuring that your organization maximizes the benefits of the cloud while maintaining operational efficiency.
Let our consultant help you find your next cloud solution